
Sustainable Tech Solutions & Cyber Security represent two critical aspects of modern-day challenges and innovations. Let’s delve into each of these topics individually before exploring their intersection:
Sustainable Tech Solutions:
Renewable Energy: The adoption of renewable energy sources like solar, wind, and hydroelectric power is a cornerstone of sustainable technology solutions. These sources produce minimal greenhouse gas emissions compared to traditional fossil fuels, thus mitigating climate change.
Energy Efficiency: Sustainable technology focuses on developing energy-efficient solutions across various sectors, including transportation, buildings, and manufacturing. This involves the use of smart systems, energy-efficient appliances, and optimized processes to reduce energy consumption.
Circular Economy: Embracing a circular economy model involves designing products and systems that prioritize resource conservation, reuse, and recycling. This approach aims to minimize waste generation and promote the sustainable use of materials throughout their lifecycle.
Green Infrastructure: Sustainable technology solutions also encompass the development of green infrastructure, such as green buildings, eco-friendly transportation systems, and sustainable urban planning practices. These initiatives aim to reduce environmental impact while enhancing the overall quality of life.
Clean Technologies: Clean technologies encompass a wide range of innovations aimed at reducing pollution and environmental degradation. This includes technologies for air and water purification, waste management, and soil remediation, among others.
Blockchain for Sustainability: Blockchain technology offers opportunities to enhance transparency and traceability in supply chains, facilitating sustainable practices such as fair trade and responsible sourcing. Implementing robust cybersecurity measures in blockchain networks is essential to safeguard against data breaches and tampering.
Cyber Security:
Threat Landscape: The cyber threat landscape is constantly evolving, with adversaries employing increasingly sophisticated techniques to compromise systems, steal data, and disrupt operations. Understanding the nature of these threats is essential for developing effective cybersecurity solutions.
Security Measures: Cybersecurity measures encompass a variety of techniques and technologies designed to protect digital assets from unauthorized access, data breaches, and cyber-attacks. This includes measures such as encryption, access controls, firewalls, intrusion detection systems, and antivirus software.
Risk Management: Effective cybersecurity involves assessing and managing risks to digital assets and systems. This includes identifying potential vulnerabilities, implementing controls to mitigate risks, and developing incident response plans to address security breaches when they occur.
Compliance and Regulations: Compliance with industry regulations and cybersecurity standards is essential for organizations to protect sensitive data and maintain the trust of their customers and stakeholders. This includes regulations such as GDPR, HIPAA, PCI DSS, and industry-specific standards.
Cybersecurity Awareness: Cybersecurity awareness and training programs are critical for educating employees and end-users about best practices for protecting against cyber threats. This includes training on how to recognize phishing attempts, use secure passwords, and safeguard sensitive information.
Artificial Intelligence (AI) in Cybersecurity: AI-powered cybersecurity solutions provide advanced threat detection and response capabilities, enabling organizations to identify and mitigate cyber threats more effectively. However, ensuring the ethical use of AI and addressing potential biases in algorithms are essential considerations in cybersecurity implementation.
Cybersecurity in Critical Infrastructure: Protecting critical infrastructure, such as power grids, transportation systems, and healthcare facilities, from cyber threats is paramount to ensure public safety and national security. Collaborative efforts between government agencies, private sector stakeholders, and cybersecurity experts are essential to strengthen the resilience of critical infrastructure against cyber-attacks.
Intersection of Sustainable Tech Solutions & Cyber Security:
The intersection of sustainable tech solutions and cybersecurity highlights the importance of integrating security considerations into the design and implementation of environmentally friendly technologies. This involves:
Secure Development Practices: Implementing secure coding practices and conducting thorough security assessments during the development of sustainable technology solutions to mitigate potential cyber threats.
Data Privacy and Protection: Ensuring the privacy and security of data collected by sustainable tech solutions, such as smart grid systems or IoT-enabled environmental monitoring devices, to prevent unauthorized access or misuse.
Resilience and Continuity: Building resilience into sustainable infrastructure to withstand cyber-attacks and other disruptions, ensuring continued operation and minimal environmental impact.
Cybersecurity for Clean Technologies: Recognizing the cybersecurity implications of clean technologies, such as renewable energy grids or electric vehicle charging networks and implementing appropriate security measures to safeguard these critical systems.
In summary, addressing the intersection of sustainable tech solutions and cybersecurity requires a holistic approach that considers both environmental and security concerns to create resilient, secure, and environmentally friendly technology solutions.
Cyber security tools used in social cyber security:
ZeroFOX: ZeroFOX is a social media and digital security platform that helps organizations protect their social media accounts from cyber threats, including phishing attacks, malware distribution, and account hijacking. It provides real-time monitoring, threat intelligence, and automated remediation.
Social-Engineer Toolkit (SET): The Social-Engineer Toolkit is an open-source penetration testing framework designed specifically for social engineering attacks. It includes various attack vectors, such as spear-phishing emails, malicious websites, and credential harvesting techniques.
BrandWatch: BrandWatch is a social media monitoring and analytics tool that helps organizations track mentions of their brand, products, or keywords across various social media platforms. It provides insights into consumer sentiment, trends, and competitive intelligence.
About Kali Linux
Kali Linux stands out as a leading cybersecurity tool, revered for its comprehensive suite of over 300 security auditing tools. As an operating system tailored specifically for security professionals and enthusiasts, it offers a versatile platform for network and system vulnerability assessment. What makes Kali Linux particularly appealing is its accessibility to users of varying cybersecurity expertise levels. Even beginners can navigate its tools effectively, thanks to its user-friendly interface and extensive documentation.
With Kali Linux, organizations gain access to a wide array of tools designed for network scanning, penetration testing, forensics, and much more. Its arsenal includes tools for discovering and exploiting vulnerabilities, testing network defenses, and analyzing security incidents. Moreover, Kali Linux simplifies the process of security monitoring and management with its intuitive interface and executable tools, allowing users to safeguard their systems with ease.
One of the standout features of Kali Linux is its availability, as it can be easily downloaded and deployed for use. Whether it’s a cybersecurity professional conducting in-depth security assessments or a beginner exploring the world of ethical hacking, Kali Linux provides the necessary tools and resources to enhance cybersecurity posture and mitigate risks effectively.
BeEF, or The Browser Exploitation Framework, is a powerful tool used in penetration testing to assess the security vulnerabilities of web browsers. In a digital landscape where web-based attacks are increasingly prevalent, BeEF provides a unique perspective by focusing on client-side vulnerabilities.
Rather than targeting traditional network perimeters or system defenses, BeEF delves into the vulnerabilities inherent in web browsers themselves. By leveraging client-side attack vectors, it allows penetration testers to evaluate the true security posture of a target environment.
BeEF works by hooking into one or more web browsers, effectively turning them into entry points for launching directed command modules and other attacks from within the browser’s context. This approach provides insights into the potential risks posed by web-based vulnerabilities and helps organizations bolster their defenses accordingly.
Overall, BeEF is a valuable tool for security professionals seeking to comprehensively assess and fortify the security of web applications and environments against emerging threats.
Getting Started with BEEF how to setup and use
Disclaimer: all the information available in this post is for educational purposes, it doesn’t have any intention to harm someone.
Step 1.
To get started with the Beef you have to install it first. The installation source code is freely available the beef is written in Ruby language. You need to set up the development environment for the ruby. After that just start the server of the beef tool using the command ./beef within the beef code directory.
Step 2.
Once the beef is started go to http://localhost:3000 in you browser you will be able to see the browser UI. Here you have to login using the username and password. By default the username and password is beef. You can change this in config.yaml file.
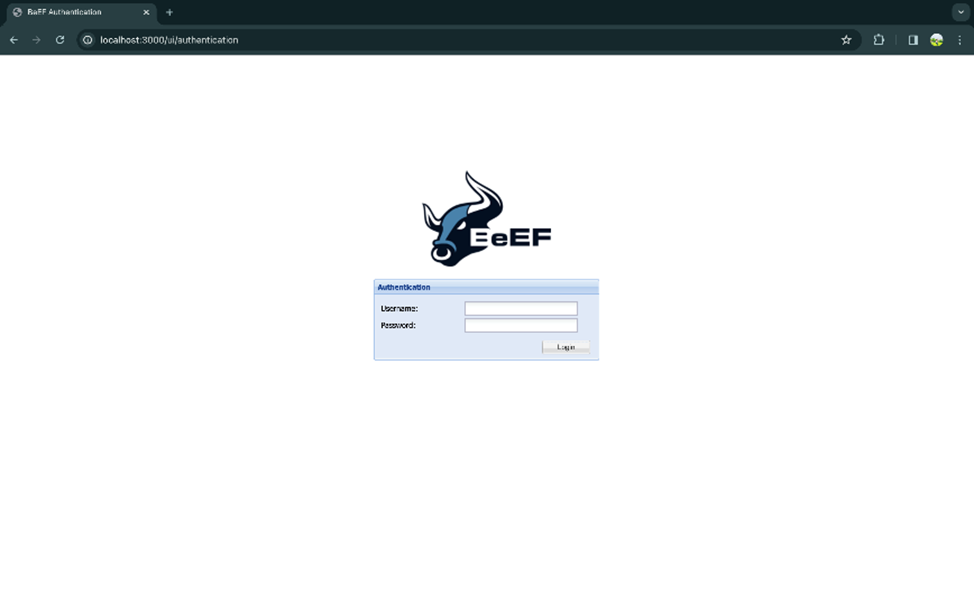
Step 3.
After login you will be able to see the page like this here same attack links are already given you can use them for target client. If you send the link and when the client click on the link you will get the access of their browser now you can perform the required attack on client.
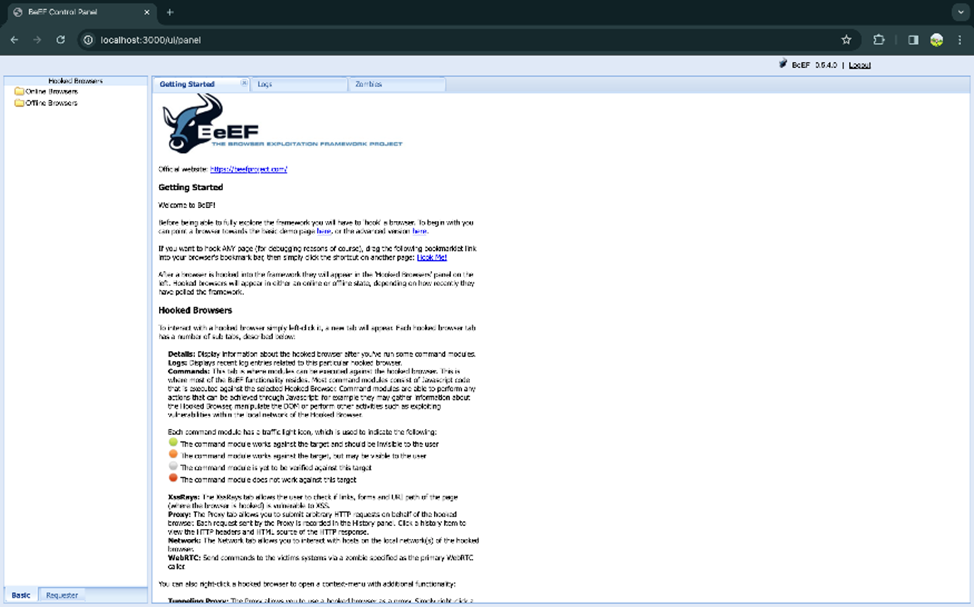
Step 4.
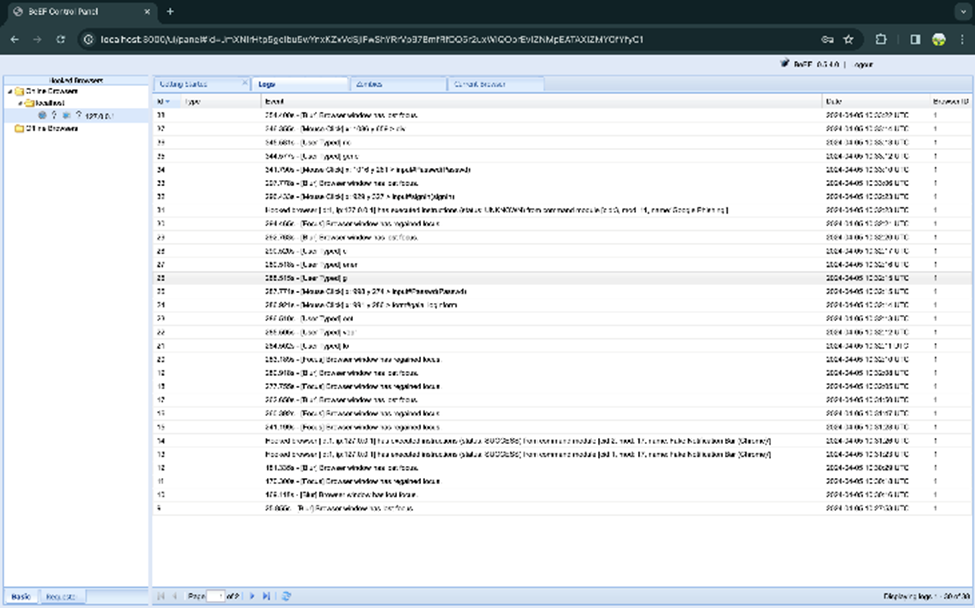
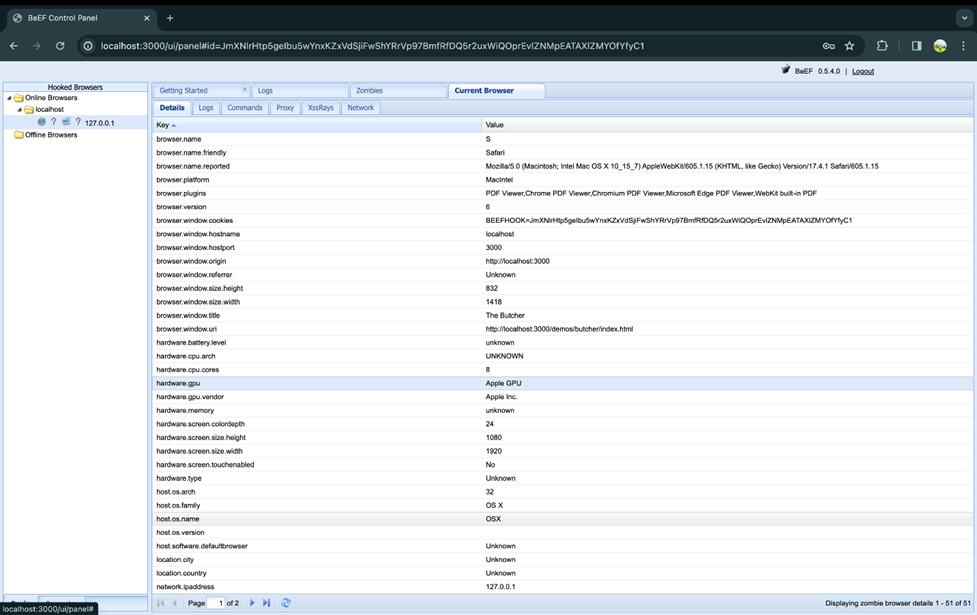
Here you will be able to see user browser history and other information in the log. In the logs you will be able to see all the action client is performing.
You can also see the device information of the target client.
How google phishing attack works in beef.
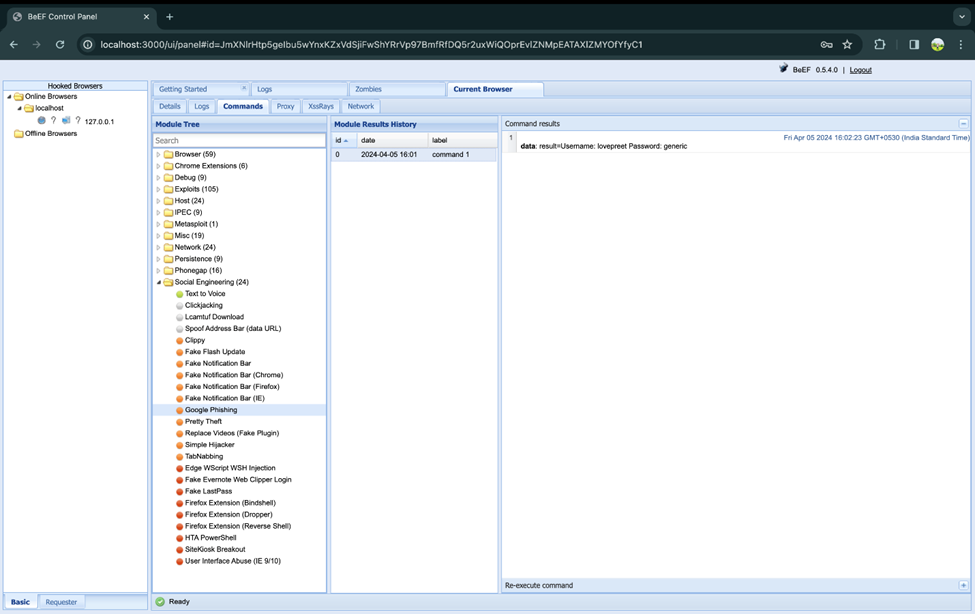
Here you will able to see a number of phishing attacks are available let suppose we choose a Google Phishing in this case it show the page same as google login when the client enter their credentials to login you will be able to see their credentials also the user will get logged-In, Even the user will not be able to identified that his username and password is shared.

Except this there are multiple type of attacks are possibe using the BEEF tool. Even the attacker can generate a QR code to share to the target client. When the client scans the QR code, the attacker will get control over the client browser.
References:
https://cyberexperts.com/cybersecurity-tools
https://ahmedulde.medium.com/installing-ruby-and-beef-on-mac-eab4f7ee32bd
